Want to be secured with your personal and professional data? Then every individual today has to have a basic idea of what cybersecurity is and how you can protect yourselves, your company, or your business. Lets face it, we all want to be secured in all directions whether it is physically or emotionally or the cyber way. Everything is interlinked with each other. If you are secured, you are happy, and in order to be secured, you need to know a few basic things about cybersecurity.
As the internet is growing everyday and the amount of time and work we spend on applications or websites or our requirements are linked to software’s and data has also increased, we should also consider safe browsing, and be secure.
If you want to understand more about the INTERNET, then you can refer to this blog post on
Lets start with what is Cybersecurity, the types of cybersecurity, and some examples to get started with the basics.
What is Cybersecurity?
- Cybersecurity, or IT security is the protection of IT systems and networks from disclosing information, or theft, or damage to either their hardware, software, or electronic data, as well as to take measures in involving any disruptions or misdirections of any services that are provided by you or your business.
- Cybersecurity analysts’ job is to protect computer networks from unauthorized access and cyberattacks performed by hackers and scammers. This work is done by trying to anticipate and guard against cyber threats, and by continuously monitoring and responding to security breaches when they do happen. Setting up alerts plays a major role in identifying any threats quickly and resolving them.
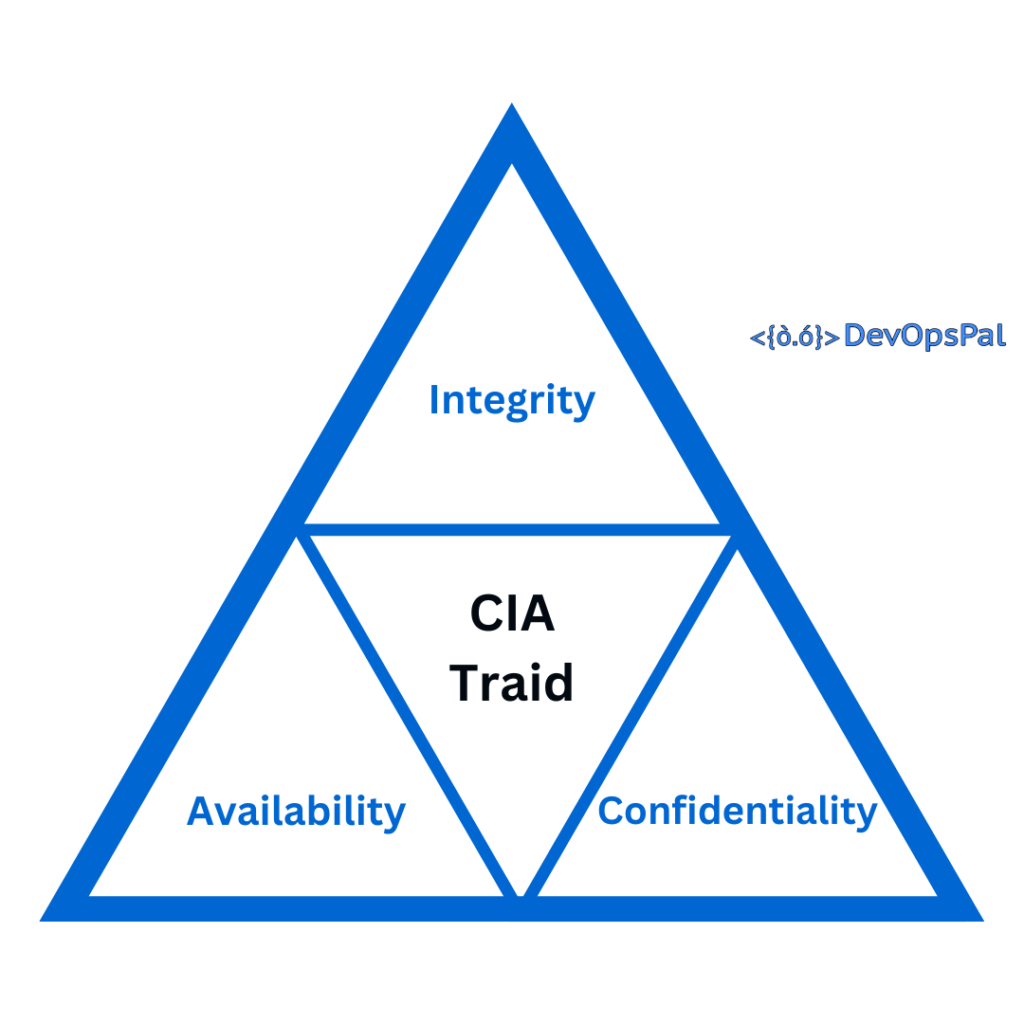
Main components of Cyber Security:
The three main components of Cyber Security are: (according to CIA (Central Intelligence Agency))
- Confidentiality
- Integrity
- Availability
Cybersecurity Types:
Let’s look into some of the various types of Cybersecurity.
- Infrastructure security.
- Network security.
- Email Security
- Application security.
- Cloud security.
- Internet of Things (IoT) security.
Let’s have a brief idea on each of these types of cybersecurity. Having a brief knowledge gives you an idea on what tasks are performed in each category. You can then go in deep on your subject of interest. I have another blog post to explain in detail on each of these topics and types.
Infrastructure Security:
Infrastructure security is the practice of protecting critical systems (which are involved in supporting the business needs) and assets against physical (workstations, laptops, smartphones, servers, routers and switches) and cyber threats.
From an IT standpoint, these usually include hardware and software assets such as end-user devices (smartphones, laptops, etc.), data center resources (file servers, print servers, email servers, etc.), networking systems (servers, switches, routers, etc.), and cloud resources (cloud applications, cloud storage and file sharing applications, etc.).
Network security:
Network security is the protection of the networking infrastructure from unauthorized access, or misuse, or theft that involves creating a secure infrastructure for usage of applications, devices, and users to work securely.
This involves having strict policies, processes and practices that are adopted to detect, monitor, and prevent unauthorized access which helps in protecting the network and data from breaches, intrusions and other threats.
Types of Network security:
- Firewalls.
- Email security
- Antivirus and anti-malware software
- Access control.
- Network Segmentation
- Intrusion prevention systems.
- Application security.
- Virtual private networks (VPNs).
- Wireless security.
- Behavioral analytics.
- Web security
- Mobile device security
Email Security:
Email security is the protection of email accounts, content, and communication between two users/organizations using different procedures and techniques against unauthorized access, loss or compromise. Emails are often used for phishing attacks, spreading malware viruses, and spam. Scammers use different ways to get your personal/business information by impersonating other users, and or try to communicate with you to transfer funds, and also try to make you click a link which has malwares to access your data.
Today’s greatest email security threat is ransomware attacks.
“When you are not sure about it, do not click or open it. Just get confirmation by another means of communication before you click on it.”

Types of Email Security:
- Spam filters
- Anti-virus protection
- Data Encryption (at rest / in transit)
- Internal/External trusted/warning messages for organizations
- SSL/TLS implementations
- Impersonation email alerts
- Additional security layer for links in emails
Application security:
Application security is the process of implementing security features to the applications by developing, adding, and testing within the applications to avoid security threats and vulnerabilities such as unauthorized access and modifications.
Application security is necessary and it is required to have proper strict authentication and authorization along with enabling audit trail features for logging and tracking.
Having a proper set of rules and policies will reduce the number of occurrences in threats.
Examples of Application Security:
Here are some of the examples of application security:
- Authentication
- Authorization
- Application security testing
- Encryption
- Logging
Cloud security:
Cloud security, also known as cloud computing security, is a collection of security measures or procedures and technology designed to address internal and external threats and to protect cloud-based infrastructure, applications, and data.
All organizations need to implement cloud security best practices as many of them are moving towards digital transformation strategy and using the right set of cloud-based tools and services will ensure data and resource access control, user and device authentication, and data privacy protection.

Types of Cloud Security:
There are four main types of Cloud Security that are needed to be considered here.
- Private Clouds
- Public Clouds
- Hybrid Clouds
- Multi Clouds
Areas of Cloud security:
The different areas of cloud security that are considered and included but not limited to are.
- Identity and access management (IAM)
- Data security.
- Data retention (DR) and business continuity (BC) planning.
- Governance (policies on detection, threat prevention, and mitigation)
- Legal compliance.
- Managing Security Monitoring, Alerting, Audit Trail, and Incident Response.
- Protecting the Network Layer.
Internet of Things (IoT) security:
Firstly, let us know what an IoT device is before jumping into the security aspects of it.
What is an IoT Device?
Any device that has an attached sensor to it (internally or externally) which can transmit data from one object to another or to people with the help of wired or wireless networks via the internet can be considered as an IoT device.
Usage of Internet of Things (IoT) devices is increasing everyday. IoT security is also necessary to keep in mind.
IoT security is the practice that keeps your IoT devices safe and the security tools protect from breaches and threats by identifying and monitoring risks and can help fix vulnerabilities.
Examples of IoT devices:
Some of the examples of IoT devices are:
- Smart devices (such as smart TV’s, watches, voice assistants, thermostats, etc)
- Smart security cameras
- Trackers for vehicles (sensors, cameras, GPS, OBD, trackers, etc)
- sensors that capture data about industrial machinery.
Types of IoT security:
- Device Authentication
- Device Authorization
- Data encryption
- Strong keys
- Firmware updates
Conclusion:
To summarize, cyber security is an important topic in today’s world and having a basic knowledge will give you better understanding to be attentive and secure. If you observe, most of the work we do is involved in cyber areas and without knowing we are using them on a daily basis in many areas. If you would like to know more about any topic in depth, then please comment with your feedback. I will be posting more content on each of the cybersecurity topics in depth. Thanks for going over the blog post and I will appreciate your feedback.

